
Mittun’s commitment to security, privacy & integrity
Mittun is dedicated to helping your organization thrive & we’re committed to keeping the web a safe place.
Mittun’s Commitment to Safety, Security & Privacy
Mittun is a professional website provider for nonprofits with a focus in visual integrations. Mittun pairs up with the applications, processes and systems you already use with an emphasis on making the entire package more effective, efficient and impactful. Being a unique service provider, Mittun doesn’t have a need to store, keep or maintain any customer data for longer than the immediate session where the data is applicable. All information used on a per-project basis and destroyed immediately thereafter. Mittun has been in business since 2010 and has maintained a 100% successful track record for keeping customer data secure and confidential.
Business Systems: Applications & Software
Mittun’s primary business infrastructure for administrative tasks is Google, which has received global security certifications and compliance verifications for Service Organization Controls SOC 2 Type II and SOC 3, in addition to complying with the ISO 27001 standard.
Google Apps for Business meets all requirements:
SOC 2 Type II and SOC 3 and ISO 27001
Google Apps for Business
- Google Documents
- Google Spreadsheets
- Google Drive
Mittun does not store any data outside of Google’s secure business applications. This is to provide assurance to our customers that the certifications and security attestations by Google keep your website safe. View more about our terms here.
View Google’s Standards, Regulations & Security Measures →
SOC 2 Type II — Pending Audit
Mittun is committed to maintaining the security of customer information. Although it’s not particularly relevant to the core of Mittun’s business model, Mittun is in the process of completing a Service Organization Controls 2 (SOC 2) Type II audit with a 3rd-party evaluator certified by The American Institute of CPAs (AICPA). This audit uses the Trust Services Principles, published by the AICPA, to evaluate the effectiveness of a service organization’s controls with respect to security, availability, processing integrity, online privacy, and confidentiality.
More information on SOC 2 reports can be found here.
Hosting and Physical Security
Mittun does not provide any servers and requires all partners to provide their own hosting environments. Mittun promotes and suggests the use of servers that are hosted on Amazon Web Services (AWS) or Google Cloud Services, such as Pantheon.io or wpEngine. Physical access to the servers is restricted to authorized personnel. Premises are monitored and access is logged with extensive documentation.
You can read further about AWS and Google security and certifications here: AWS, Google
Further security measures include:
- Company issues computers, secure passwords and two-step authorization
- iPhone with TouchID or FaceID, 6-digit passcode or 8+ character password
- Two-step Authorization required for all login portals
- Mittun’s Headquarters in Santa Monica is controlled & monitored 24/7/365 via video surveillance and on-site security officers
- All backups are securely encrypted via HTTPS and stored off-site via Google Drive, Dropbox or AWS.
- Mittun is committed to energy efficiency and going Green. For that reason, we are a 100% paper-free by-choice company. All physical and/or paper documents we receive are safely destroyed via Iron Mountain shredding: They are securely picked up, taken off-site and destroyed daily via their automated and secure service.
- All past employees are required to forfeit company devices, keys, cards and all logins are immediately changed and ownership is transferred to an executive at Mittun
In an effort to improve all of Mittun’s internal operations, we have committed to withhold the following practices in everything we pursue. This includes:
- Strong Data Security Policies
- Extensive Staff Training
- Physical Office Security
- Thorough Documentation
Physical Technology
Company-issued computers to all full-time staff with two-step authentication required. iPhone with fingerprint required access or 6-digit passcodes is mandatory. Mittun makes it virtually impossible for non-Mittun team members to access Mittun-only information.
People
Mittun only partners with top talent and people committed to integrity. Background checks are conducted annually by a verified 3rd-party vendor for all Mittun employees.
Physical Space
Our headquarters is located in downtown Santa Monica with 24/7/365 on-site security personnel and surveillance cameras. Mittun’s office is gated behind 3 keycard-only access points plus a keycard-only elevator. Even the security guard on the first floor can’t access the office on the second.
We-don’t-and-we-won’t store your passwords security policy
Mittun refuses to store sensitive customer data. We require and suggest the use of resetting passwords via the application’s API so only the relevant email address has access to the password.
No public computers
Mittun refuses to connect to anything not under a secure, controlled environment.
Two-Factor Authentication
Mittun enforces the deployment of two-factor authentication for all local and remote websites, applications and software that require a username and password to access.
HTTPS & SSL
Mittun’s forward facing website is encrypted by the industry standard security protocol, HTTPS. This means that all data is encrypted & transmitted via Secure Socket Layers (SSL) and we have a signed SSL certificate with GoDaddy.
Isolation of Services
Mittun’s internal servers run in Linux virtual machines which are isolated from one another and from the underlying hardware layer using Google’s cloud computer technology. Server processes are restricted to a particular directory and do not have access to the local filesystem. No customer data is ever stored on Mittun’s internal servers.
File Systems and Communication
All pages containing sensitive data related to customers or user data are restricted to HTTPS encrypted connections served through Google’s Secure Business Applications. All access to the Mittun API is restricted to HTTPS encrypted connections. All data retrieval from Stripe is done via Stripe Connect using your Stripe Account ID and two step autorization. All data retrieval from Stripe is done with your Stripe Account ID over a secure connection with Stripe’s API. All data retrieval from ACH transfers is done via Citibank’s Online Secure Center. All data retrieval from Citibank is done over a secure connection with Citibank’s API. Any webhooks Mittun sends to production systems are required to use HTTPS and never transfer company data.
User passwords are secured with vault-based encryption software. They are never stored in the database in plaintext and are not readable by staff, instead, as is standard practice, only a secure hash of the password is stored in the database. Because the hash is relatively expensive to compute, and because a “salting” method is used, brute-force guessing attempts are relatively ineffective, and password reverse-engineering is difficult even if the hash value were to be obtained by a malicious party. Clients are required to have reasonably strong passwords. Passwords do provide access to the Mittun website and various applications controlled by Mittun, however, and it is the responsibility of the end user to protect this password with care.
Integrations with Stripe are facilitated via their official OAuth applications: Stripe Connect. You can revoke Mittun’s access at any time via your Stripe Dashboard, if applicable. If making payments via ACH at the bank-to-bank level, then this is irrelevant.
For certain integrations we may ask for an API key or login credential with minimal permissions, as well as additional webhooks. The API key or login credential we store securely in Google’s Vault will be encrypted and will never be revealed to the end user or to Mittun personnel. You can change or remove these credentials at anytime in order to remove access.
Employee Access
No Mittun staff will access your organization’s metrics unless required for support reasons. In cases where staff must access the dashboard in order to perform support, we will ask for your consent, except when responding to a critical security issue or suspected abuse.
When working a support issue we do our best to respect your privacy as much as possible, we only access the minimum data needed to resolve your issue.
Credit Card Safety
When you register your credit card with Mittun, your credit card data is not transmitted through nor stored on our systems. Instead, we depend on Stripe. Stripe is certified to PCI Service Provider Level 1, the most stringent level of certification available. Stripe’s security information is available online. Mittun will never keep your CC data on file, ever.
Development Process
Mittun developers have been trained in secure coding practices, requiring to always build with at least 3 public environments for development, testing and production. “If it’s not in 3 places, it doesn’t exist” — this is Mittun’s law of controlling, backing up and handling website files and content.
The Mittun website architecture works best when paired with an innovative hosting platform that allows for the production of 3 website environments, with automatic backups and malware-blocking in place. All of Mittun’s preferred hosting partners include mitigation measures for common security flaws such as the OWASP Top 10. The Mittun website architecture uses WordPress, which is the industry standard, high-strength website framework with the world’s leading development teams contributing to the ongoing security and stability of the platform. Periodic security tests are conducted on all Mittun-owned websites as well as customer websites Mittun is contributing to, including using scanning and fuzzing tools to check for vulnerabilities.
Reporting System Failures and Breaches
If at anytime you become aware of a system failure or breach, please contact us immediately at: info@mittun.com
Business Systems: Internal Operations
——————————————————————————————-
Website Hosting Requirements
Antivirus
Mittun requires that all website hosts provide antivirus protection bundled into the platform itself to ensure the system’s integrity and to prevent malware from spreading through customer websites.
Backups: Manual via Mittun
Backups are maintained and held at the server level. Upon request, Mittun will download a backup to a local hard drive and manually upload the backup to an off-site document storage specialist, such as Dropbox, upon request.
Perks of Pantheon as a service provider for web hosting:
- Secure Infrastructure
- Resource Isolation
- Automated Site Monitoring
- Network Intrusion Protection
- Denial of Service Protection
- SAML and Two-Factor Authentication
- Role-Based Access to Site Resources
- Anti-Malware
- Pantheon Employee Administrative Access
- Releasing Patches and Updates
- Vulnerabilities and Incident Response
- Datacenter Security
- Redundancy
- Customer Content Durability
- Backups
- Disaster Recovery
- The Family Educational Rights and Privacy Act (FERPA) Compliance
- SOC 2 Type II and SOC 3 and ISO 27001
- Privacy Shield & US-Swiss Safe Harbor
View all the details of Pantheon Security: View →
View Pantheon’s SOC 2 Type 2 Certificate Report: View →
Other Web Platform Hosts:
GoDaddy Website Hosting: View →
View GoDaddy’s Subsidiary, Sucuri Security: View →
—–
Third-Party Security Assessments
Mittun is a cloud-based company utilizing best-in-class business tools with world class security. All primary tools and services used by Mittun have undergone extensive third-party security assessments and audits. Mittun serves as a pass through entity for data collection Mittun does not store any data directly, Mittun does not have any servers on site and leverages cloud based applications for all operational procedures. All
The primary applications and tools used at Mittun re:
Google Business: View Google Infrastructure Security Design Overview →
Google Cloud: Google Clould Soc 3 Report →
Google Cloud: Google Cloud Soc 2 Report →
GitHub: View Github Soc 3 Report →
GitHub Security: View GitHub Security Page →
Pantheon: View Pantheon Security Page →
1Password: View 1Password Security Page →
Slack: View Slack’s Security Page →
Atlassian + Trello: View Trello’s Security Page →
Mittun Security Training Protocols
Security measures are deployed throughout Mittun’s entire operational ecosystem, from the physical devices we use to the code we write, to the cloud-based servers that transfer the data.
The only thing worse than a cyber attack is multiple cyber attacks. Mittun focuses on prevention and preparation to ensure that there is a proper incident response plan in place if worst comes to worst. All of Mittun’s websites, platforms and services have a 99.99% uptime guarantee. However, we must have a recovery plan in place for the 0.01% so our partners can rest easy knowing that edge-cases are accounted for.
Our Philosophy: Security & privacy protection by design and default.
Our training philosophy focuses on extensive training for the following key areas, upon hire and quarterly.
- Passwords & Authentication
- Mobile Device Security
- Cloud Security
- Internet Use
- Email Use
- Working Remotely
- Security at Home
- Public WiFi
- Phishing Attacks
- Removable Media
- Physical Security
- Social Engineering
- Social Media Use
- Customer Files, Media & Digital Assets
- Code & Database
- Handling Customer Login Credentials
- Trade Secrets & Internal Processes
- Project Management Protocols for Security
Additionally, Mittun trains partners, clients and customers on website management & security best practices.
Mittun Cyber Security Incident Response Plan (MCSIRP)
Mittun is committed to security, protection and reliability of all digital products and services. Mittun has adopted the 4 key phases of an effective incident response plan as determined by The National Institute of Standards and Technology (NIST).
- Preparation
- Prevention
- Detection & Analysis
- Identification
- Containment, Eradication & Recovery
- Post Incident Activities
- Improvement Plans
Detailed documentation on how to handle incidents can be found on the NIST.gov website here: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
If you are aware of a cyber attack, data breach or anything preventing a service to be operating as intended, please email info@mittun.com and support@mittun.com immediately with your findings.
Network Configuration Diagrams — Development Workflow
Codebase and database is configured as follows;
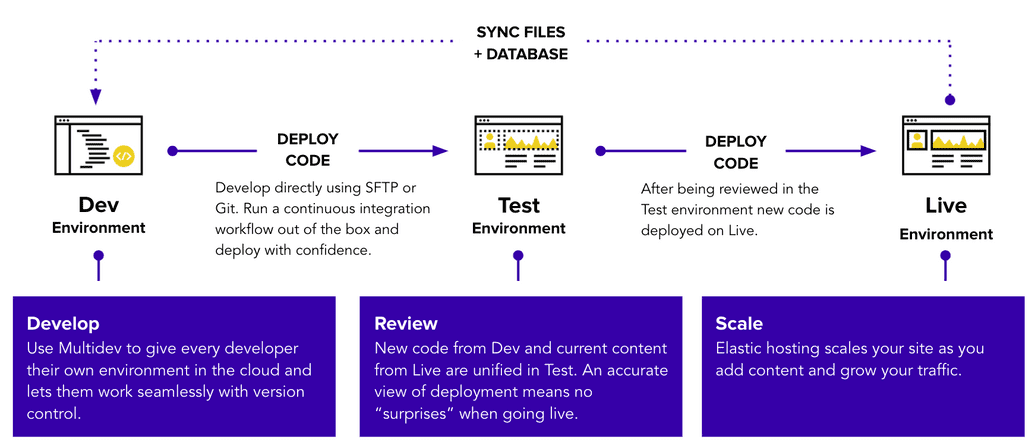
Code & Database Workflow
Classy API Data Flow & Configuration Diagram
Classy Data flows from Classy’s API to the Database, as follows:
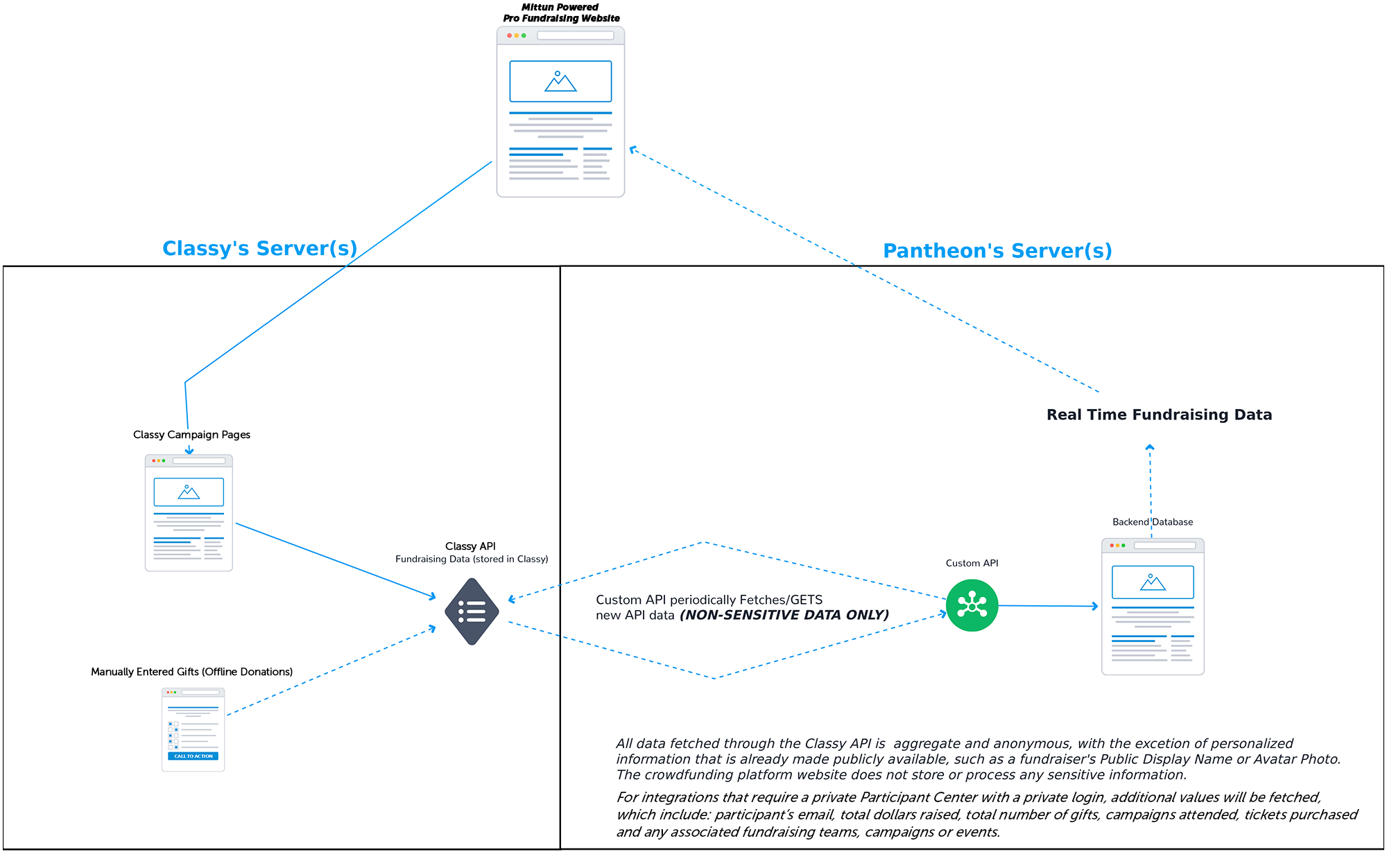
Classy API Data Flow
Mittun’s Physical Offsite Storage Policy (MPOSP)
Mittun operates on the cloud. Every employee has a physical device that is only accessible via two-step authentication by the individual employee. The devices are never shared and are used by one unique employee only.
All cloud-based data that is saved locally is only to be used on a per-session basis and local copies cannot be saved beyond the immediate session. All data is end-to-end encrypted and cannot be intercepted.
Mittun only allows offsite storage to be used if the data is encrypted, hashed and is password-locked with two-step authentication. The device must be a modern day SSD and placed in a fireproof safe in a locked building that is fully insured.
Mittun takes encrypted, aggregate backups weekly and on a per-account basis as-requested only.
Vulnerability Management Policy
This policy defines requirements for the management of information security vulnerabilities and the notification, testing, and installation of security-related patches on devices connected to any connected networks.
Unauthenticated Network Vulnerability Scans
Mittun’s platforms routinely undergo scheduled scans that look at the entire networks and digital ecosystems, at least once monthly.
Authenticated Network Vulnerability Scans
All network, systems, databases and applications that create, process, maintain, transmit or store data must be scanned on a regularly basis, at least once monthly.
Version & Change Control Policy
Mittun’s change control process can be applied to the visual assets we create to the code we develop, and everything in between.
- All changes must be documented and dated.
- All changes must follow the change control process
- All code-changed must be done on a Development environment prior to pushing to Production (LIVE)
- All commits must be detailed and specific to code being added/modified/removed
- Commits shall never be bundled so every commit is unique to the feature/fix it was intended for
- Automatic daily backups at the server-level must be applied for all website platforms
- Hotfixes are only accepted on an as-emergency basis and must be documented in the next code commit and must be signed-off by the customer prior to doing so and is only warranted under extreme circumstances & edge cases as defined here.
- Copies must be made of all unique files.
- Original versions must be maintained for historical reference.
- Version numbers must be applied to every new version of a file that is saved
- Version control systems like GitHub must be used for all code that is deployed.
- Images and visual assets must also be named with version number.
The general framework for proposing and implementing changes is as follows:
- Initiation (Propose change).
- Assessment.
- Analysis (Decision).
- Implementation (Make change).
- Closure.
Coding Standards
Mittun’s follows modern day coding standards and best practices for control, speed and security.
We believe in clean code that is well-commented, fast and human friendly whenever possible. All code must be properly version-controlled using GitHub, as defined above.
Mittun’s coding standards can be viewed on Google’s Developer Documentation Guide as well as defined on w3 Schools, the world’s largest developer site.
Google Developer Documentation Guide →
Privacy Policy
Risk Assessment Program
1. Project Scoping and Planning:
- Risk Identification: Identify potential risks in the project’s scope, including technical, legal, and financial risks.
- Risk Evaluation: Assess the likelihood and impact of identified risks.
- Risk Mitigation: Develop strategies to minimize or eliminate risks, such as clear project requirements, legal compliance checks, and budget planning.
- Resources:
- Project Management Institute: PMI Risk Management
2. Technical Risks:
- Security Risks: Identify vulnerabilities in the website and API integrations, such as data breaches, unauthorized access, and malware.
- Risk Evaluation: Conduct security assessments and penetration testing.
- Risk Mitigation: Implement security measures such as encryption, firewalls, and regular security updates.
- Resources:
3. Legal and Compliance Risks:
- Data Privacy: Ensure compliance with data protection regulations (e.g., GDPR, CCPA) when handling user data.
- Intellectual Property: Verify the proper use of third-party content and software licenses.
- Risk Mitigation: Conduct legal reviews and implement compliance policies.
- Resources:
4. Third-Party API Risks:
- Integration Risks: Assess the reliability and security of third-party fundraising APIs.
- Data Integrity: Ensure accurate and secure data transfer between the website and APIs.
- Risk Mitigation: Perform thorough API testing, establish secure API connections, and monitor API performance.
- Resources:
- API Security: OWASP API Security
5. Financial Risks:
- Budget Overruns: Monitor project expenses to prevent exceeding the budget.
- Funding Disruptions: Plan for potential interruptions in funding for nonprofit projects.
- Risk Mitigation: Implement financial controls and regularly review project budgets.
- Resources:
- Financial Management for Nonprofits: Nonprofit Financial Stewardship
6. Stakeholder Engagement Risks:
- Communication Risks: Ensure clear and consistent communication with stakeholders, including nonprofits, donors, and team members.
- Expectation Management: Align project goals and expectations with all stakeholders.
- Risk Mitigation: Develop a communication plan and engage stakeholders regularly.
- Resources:
- Stakeholder Engagement: Stakeholder Engagement Strategies
7. Monitoring and Review:
- Regularly review and update the risk assessment program to address new risks and changes in the project environment.
- Conduct post-project reviews to identify lessons learned and improve future risk management practices.
Conclusion: Implementing a comprehensive risk assessment program is essential for a digital website agency working with nonprofits. By addressing technical, legal, compliance, financial, and stakeholder engagement risks, the agency can ensure the successful delivery of custom websites that safely and effectively integrate with third-party fundraising APIs.

